Last November, Google Cloud announced a technological advance it had begun in 2011, presenting itself as part of the zero-trust principle, called "Beyond Corp", which would ensure better security for their corporate customers' data. [1]
What is Zero Trust?
In August 2020, the US NIST produced a standard of architecture recommendations on Zero Trust.[2]
In 2021, the Zero Trust strategy was the subject of two leading French publications:
The Zero Trust concept is not a turnkey solution, but an Implicit Trust model focused on the user, based on dynamic and granular controls:
- access to resources must be granted on a need-to-know basis;
- access must be granted on the basis of the lowest level of privilege required to perform the task;
- access requests must be controlled in the same way regardless of their origin (the entity's "internal" or "external" perimeter);
- the resource access policy must be dynamic, taking into account a wide range of attributes (identities of the accessor and the resource accessed, sensitivity of the resources requested, user behavioral analysis, access times, etc.);
- the entity must ensure the security of all its assets at the time of access requests and on a recurring basis during use;
- Authentications and authorizations to access resources must be regularly reassessed.
Finally, in November 2022, the US DoD issued its Zero Trust strategy.[5]
We asked artificial intelligence ChatGPT to define these principles... and the result is incredibly relevant.
The zero-trust principle is a security approach in which no user, device or service is automatically trusted, even if they are within the protected network zone. This means that all access requests are authenticated and authorized before being granted, regardless of the user's location or prior knowledge. This principle is often used to reinforce the security of corporate networks and cloud systems.
The zero knowledge principle, on the other hand, is an approach to data confidentiality that protects sensitive information while keeping it accessible to authorized users. It's an encryption method that allows a third party to verify the information without being able to read it. This means that data is encrypted in such a way that only the owner can decrypt it, even if it is stored or transmitted by a third party. This technique is often used in cloud storage systems, encrypted messaging systems and online payment systems.
Zero Trust": a breakthrough principle finally on the agenda!
The good news in this Google Zero Trust communication is that, following on from NIST and DoD, and a month after Apple announced the availability of end-to-end encrypted storage on i-Cloud[6]a new GAFAM pillar officially recognizes that a new layer of end-to-end security is needed to confidently use its cloud-hosted data servers.
At a time when cyber threats have never been greater (espionage, sabotage and extra-territorial judicialization), at a time when Europe wants to impose digital sovereignty on its Administrations, Companies and Citizens, talking about security, and Zero Trust in particular, is finally becoming an obligatory sales argument that is arriving in force on the market and becoming essential for selling secure quality service on the Cloud.
Security according to Google: "Have confidence!"
We have to admit that talking about Zero Trust, as Google does in this techno-marketing article, is a bit of a trick!

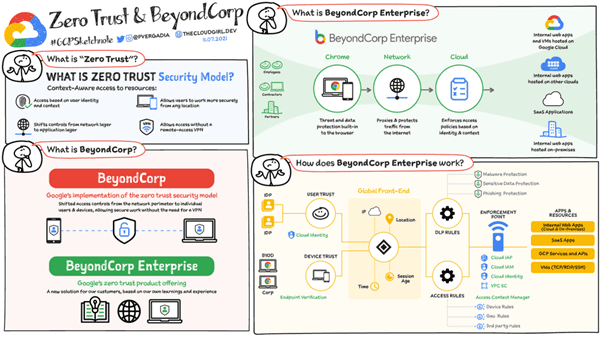
At best, we can speak ofGoogle Trust". Google's approach is based on a classic vision of security, in which only what's in the internal network is trusted, even though Beyond Corp provides an undeniable layer of fine-grained rights management at network level.
Google's Zero Trust is a security model based on the permanent verification of network requests, but delegated to a third party, in this case Google. Trust Google!
But is ZERO TRUST just that?
In the end, the "Beyond Corp" approach is nothing more than a classic implementation of rights management that relies on a new Google intermediation and feed filtering service.[1]
Zero Trust according to Google = Google Trust
Google's approach is based on a fairly basic information system that is still based on identity and flow control by a proprietary trust system that accesses all information.

The problem with this approach is that you always have to trust three spies:
- the honest but curious in-house admirer
- cloud provider Google
- the US administration and US extraterritorial laws.
In this vision, we are moving from an intranet where everyone has access to everything, to a Zero Trust approach, which amounts to saying :
"Please implement satisfactory access control at last."
This approach is necessary, but not sufficient, because its implementation involves trusting a single external player, namely Google, and behind it the framework set by the US administration.
Even if it protects against certain external cyber threats in particular, the main cyber threat, extraterritorial judicialization, is by no means converted. Thus, a dishonest administrator could change the data without the owner's approval, and an honest but curious administrator could read the data over the shoulder of its rightful owner.
But who REALLY holds the keys to my data?
Zero Trust according to Parsec = end-users trust only themselves
The Parsec approach[7] [8] is, on the contrary, "ultimate" Zero Trust [9] and Zero Knowledge [10], where trust is never delegated : the user remains the sole and ultimate master of his data.

Beyond the initial impression of a marketing catch-all or buzzword, the Zero Trust concept actually embodies a fundamental notion of IT security that goes far beyond what current centralized web-based architectures can deliver.
This concept consists in defying all intermediaries: cloud providers, outsourcing service providers, network or Internet infrastructure providers, "honest but curious" system administrators, extra-territorial laws and, on the contrary, entrusting the end-user with the responsibility for his or her own security, including data security, at hardware, human and software levels.
Threat comparison between the two "Zero Trust" models

[1] https://cloud.google.com/blog/fr/topics/developers-practitioners/le-zero-trust-et-beyondcorp-de-google-cloud?hl=fr&pref=k
[2] SP 800-207 Zero Trust Architecture: https: //csrc.nist.gov/publications/detail/sp/800-207/final
[3] https://www.ssi.gouv.fr/agence/publication/le-modele-zero-trust/
[4]https://www.cigref.fr/wp/wp-content/uploads/2022/02/Vers-une-philosophie-Zero-Trust-Une-rupture-dans-la-continuite-pour-la-securite-des-applications-fevrier-2022.pdf
[5] https://dodcio.defense.gov/Portals/0/Documents/Library/DoD-ZTStrategy.pdf
[6]https://www.apple.com/newsroom/2022/12/apple-advances-user-security-with-powerful-new-data-protections/
[7] Open source software: https: //github.com/Scille/parsec-cloud/
[8] ANSSI CSPN-certified software: https: //www.ssi.gouv.fr/entreprise/certification_cspn/parsec-version-2-0-0/
[9] No one but me has the key to my data.
[10] No one but me has access to my unencrypted data.





