KEY FIGURES
The blockchain is nothing more than a chained list of blocks whose reliability and the continuity of the information they contain are guaranteed by the links between them (see part 1).
It's a technology that emerged in the 21st century to decentralize bank transfers. It came to prominence with the rise of cryptocurrencies, but it is above all a technology that enables sustainable, secure, decentralized storage of information.
Indeed, blockchain does not require you to trust a third party: we're talking about zero-trust and zero knowledge security.
In this context, blockchain is a particularly useful technology for companies wishing to store sensitive data securely in the cloud. Zero trust security combined with zero knowledge encryption represents the future of cybersecurity for sensitive data, and is becoming a fundamental requirement for all companies that are increasingly turning to the public cloud to store their data.
Hatching functions
What happens when you enter your login and password on a website?
Your username lets them know which account you want to log in to, and your password is what lets them know it's really you.
But of course, the website doesn't keep a database of its users' passwords, out of concern for IT security. So how can the website verify that your password is the right one when it doesn't know it?
The website, like the blockchain, uses a hash function.
A hash function is a mathematical function that transforms an input text (a password, for example) into another unreadable text, called a signature.
A hash function is different from an encryption function. Whereas an encryption function must have a reciprocal, i.e. an inverse function that transforms a coded message into a readable one, a hash function must not be able to admit a reciprocal. The aim of such a function is to drown out the information, so that it cannot be traced back even with knowledge of the fingerprint and the internal mechanisms of the hash function.
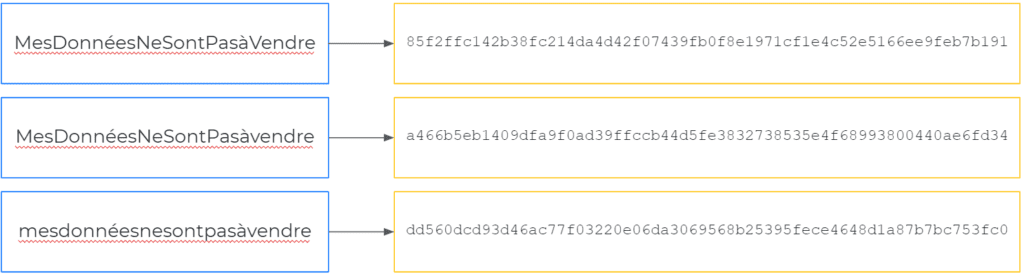
To achieve this, hash functions are extremely sensitive to the smallest details. Below is the result of the SHA256 hash function (used for many cryptocurrencies as well as parsec.cloud) applied to various entries. As you can see, simply changing a capital letter to lower case completely alters the resulting signature.
But what does the website where I enter my password do? Precisely, it doesn't store the password, but calculates its signature: the hash. Since no one can trace a password back to a hash, hashes can be stored in an online database. So the site compares the password hash I gave it with the password hash stored when I created my account. It finds that the two signatures are identical, and so the authenticity of my connection is established.

Hash function and blockchain
At the same time, the hash function is also the central tool of the blockchain. It links blocks together and secures the blockchain through the work of miners.
In fact, each block in the chain stores the hash of the previous block. In this sense, the blocks form a chain. As the hash function is highly sensitive to the slightest modification, the data stored in the previous block cannot be altered by a user of the blockchain, or all the blocks that follow will have to be modified.
In this way, the blockchain exploits a first property of hash functions: their "sensitivity" to the slightest change in the input variable. Proof-of-work, an innovation brought about by Bitcoin, exploits another: that of the impossibility, given a hash, of finding an antecedent to it.
Indeed, what miners are asked to do is almost the impossible: find an antecedent to a hash. Specifically, the miner must find a text (a character string) which, added after the miner's data and signature, causes the hash of the total block to begin with a predefined number of zeros. The choice is arbitrary: why zeros, how many, etc.

Trying to do this by hand for SHA256 so that the hash of a fictitious block begins with a single zero, we see that we have to get to the 13th try. But, of course, the complexity increases exponentially both when looking for several zeros in a row and when the file preceding the proof-of-work grows in size (the size limit of a Bitcoin block is 1 MB, i.e. around 64,000 times larger than "ProofOfWork:"). On July 15, 2020, around 123 billion billion hashes per second were tested.
But this artificial complexification of the Bitcoin blockchain is the reason it works, since without this proof of work, blocks would be mined every minute if not every second, making the operation of synchronizing the blockchain between miners only that much more delicate.
Since current hash functions do not admit of an algorithm capable of tracing a result back to its antecedent, the only possible approach is to test myriads of strings until the proof of work is found: the one that allows the hash of the entire block to begin with, say, 20 zeros. These serial tests are precisely what Bitcoin miners do, equipping themselves with thousands of euros worth of graphics cards and processors, and it's this energy expenditure that is accompanied by crypto-monetary compensation.
Data security thanks to blockchain
As centralized security architectures become more vulnerable to attack and data leakage, it's vital to understand the technologies that will enable us, now and in the future, to live in an increasingly connected world without sacrificing our private and professional lives.
Even though blockchain has made a name for itself via cryptocurrencies, and in particular Bitcoin with its proof-of-work algorithm , it is above all a decentralized storage solution that guarantees the durability and unforgeability of the data it contains .It can therefore be put to good use for cloud storage of sensitive data.

PARSEC is a software solution designed to optimize the security of sensitive data stored in the cloud. The PARSEC R&D team is currently working in partnership with the French Atomic Energy Commission (CEA ) to integrate blockchain into PARSEC, so as to further optimize the Zero-Trust and Zero-Knowledge security offered by the software.
What's it all about?
This research project, the only one of its kind in the world, adds a direct attack on the metadata server to the PARSEC security model.
To counter this attack, the aim is to decentralize the metadata server by integrating it into a blockchain. The federation of metadata servers is then able to detect and correct any attack on one of the servers.
To create a blockchain using metadata servers, PARSEC and CEA opted for the open source tool Hyperledger .
 Gaspard Sagot ; R&D intern in applied cryptography at SCILLE.
Gaspard Sagot ; R&D intern in applied cryptography at SCILLE.
Sources