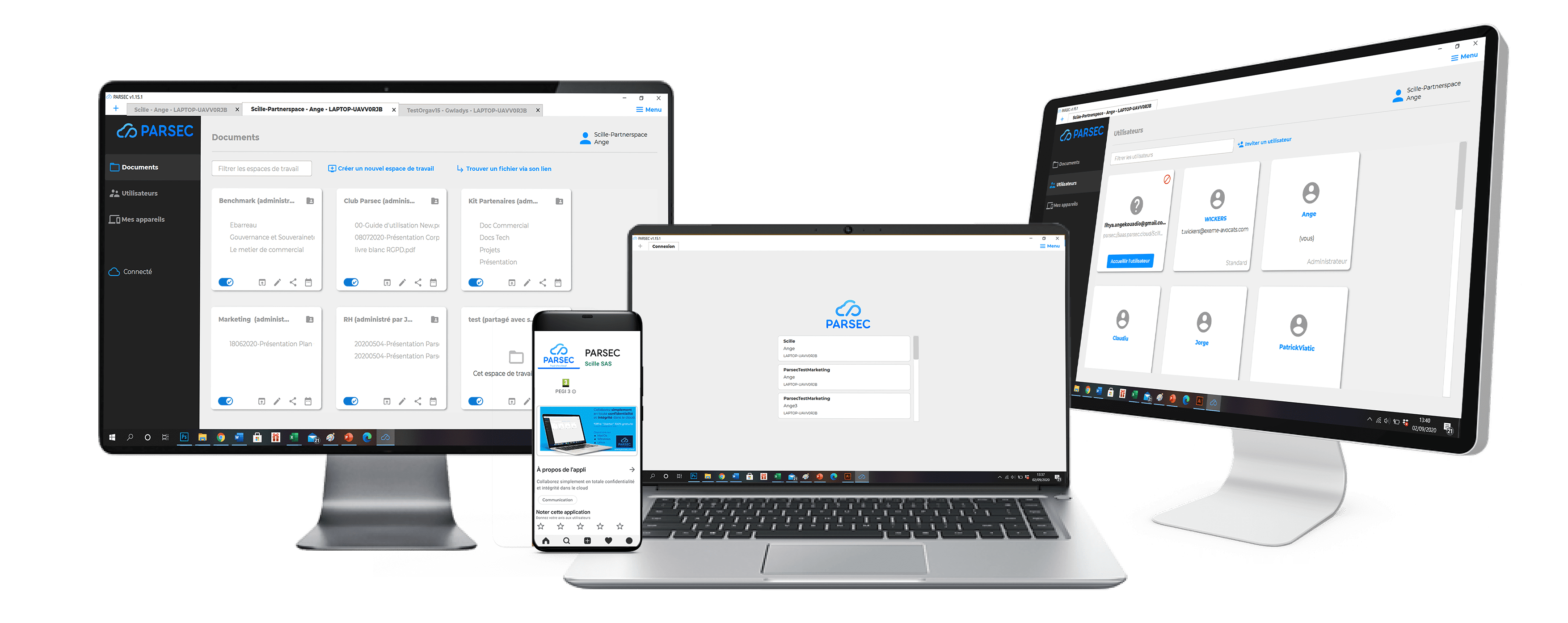
Dive into the innovation
in security
With the best of technology combined with the best of security


Make intrusion totally impossible
With our unique end-to-end data encryption technology, you'll make intrusion impossible, both during transmission and storage. The sensitive file is not only locked with keys that are only available to authorized users, but it is also sliced so that each piece of data is encrypted. Thus, if a malicious software intercepts the confidential document, it will only discover a perfectly unreadable fragment.
Get your mathematical proof authenticated
Our Zero Knowledge innovation authenticates authorized users, without requiring their identity to prevent it from being disclosed. The certification is done by an entity, called a "proof provider", which mathematically proves to another entity, the "verifier", that a proposition is true without revealing any information other than the truth of the proposition itself.
Discover the PARSEC technology in video
Protect your sensitive data with security innovation
Certification of your workstation
considered as the only trusted entity
Splitting your files into several blocks
stored on different public or private clouds
End-to-end encryption of each chopped block
to block the privileges of unauthorized users

"Anticipating future needs and integrating security by design, while remaining very easy to use, PARSEC has a software architecture based on concepts and algorithms from Research, which guarantees :
- Privacy
- Integrity
- Resilience
- Availability "
"Developed by Scille in collaboration with the Laboratoire Bordelais de Recherche en Informatique, PARSEC is a state-of-the-art solution.
Thierry Leblond, CEO & Co-founder of PARSEC

Advice from our cyber security experts
Parsec V3: from Python to Rust, why and how?
Introduction The Parsec tool was originally developed in Python. This interpreted language is easy to read and enables rapid development and iteration. It also has the advantage of running natively on all major desktop platforms...
ANSSI assesses the IT threat to law firms
Did you know? ANSSI notes that the scope of cyber-attacks on law firms is constantly expanding, notably due to the increasing digitalization of the profession and legal procedures. Lawyers and law firms are frequently the target of...